What is risk management?
Risk management is the systematic approach and practice of managing uncertainty to minimize potential harm and loss and maximize potential opportunities and gains. The goal of risk management is “to set the best course of action under uncertainty by identifying, assessing, understanding, making decisions, and communicating risk issues.” Risk management is inherently an enabling process: rather than provoking decisions to stop programming, effective risk management processes create the conditions necessary for the program to proceed, and, indeed, succeed. See resource below.
What is a risk in the context of a project?
The International Organization for Standardization (ISO) defines risk as “the effect of uncertainty on objectives.” The effect can be positive (provide benefit/opportunity) or negative (serve as a threat, provoke damage). Accordingly, a risk involves a deviation from the expected.
Why is risk management important for P/CVE projects?
There are risks in implementing any P/CVE activity. Therefore, consider a proactive approach to identifying and responding to risks throughout project implementation.
Two Features of the P/CVE Field that Make Risk Management Essential
|
The potential for negative or positive impact is especially high. If risks are not identified and planned for in a P/CVE project, the potential for harm to individuals, communities, and the organization can be significantly increased. On the other hand, if we identify and manage risks to help the project improve activity prioritization, effectiveness, and efficiency, individuals and communities involved in a P/CVE project can become more resilient to VE in their communities. |
There is an increased likelihood of risk when working on P/CVE. When operating in conflict-affected locations or in at-risk areas for VE, you are working on issues that are often misunderstood, controversial, and polarizing. This raises risks related to organizational reputation and staff security. Also, since P/CVE is a relatively new field, there are ongoing debates and ambiguity around key definitions, the factors that drive VE, and what works or doesn’t work when it comes to P/CVE programming. |
By identifying and managing risk in a P/CVE project, you are mitigating possible negative impacts and enhancing the potential for effective implementation and positive impact of your project, while protecting your community, project beneficiaries, team, and organization.
While risk management approaches differ from one project or organization to another, such approaches typically include the steps outlined in the table below.
|
STEP 1 |
Usually you identify "categories of risk" to make sure you are considering different parts or phases of the project. These categories could include: operational risks; contextual risks; security risks; institutional risks; and programmatic risks. |
|
STEP 2 |
For each risk identified, answer two key questions:
Using this assessment, your team can numerically score or rank (low, medium, high) the probability/likelihood and expected impact of a risk. The results of this assessment are often presented in the form of a risk matrix, with probability and impact on different axes, to show which risks are the most important to consider. |
|
STEP 3 |
Develop a plan for how to respond to these risks. Most of the time, risks cannot be eliminated and the response should identify how to manage these risks. Possible responses usually involve one of the following methods:
|
This table draws on the overview of risk management provided in the Operational Guidelines on the preparation and implementation of EU financed actions specific to countering terrorism and violent extremism in third countries.
There are several risk management frameworks and tools that you can draw on for your project. UNDP’s Risk Management for Preventing Violent Extremism (PVE) Programmes: Guidance Note for Practitioners describes five key steps (see graph below) for applying a risk management process to your P/CVE project. Click on this quick reference document summarizing the five steps of UNDP’s risk management process.
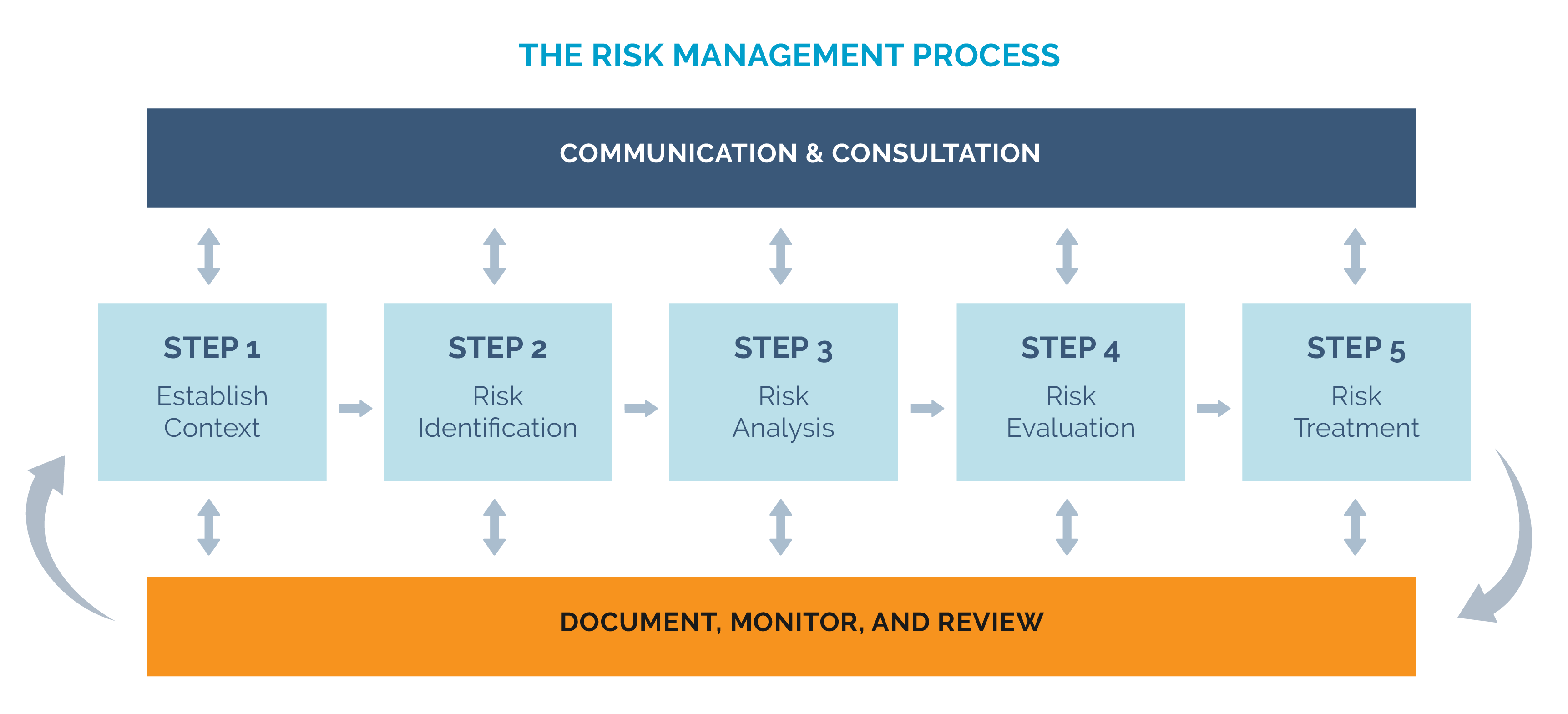
Check out this example of a Risk Register adapted from the UNDP’s guide. This risk register will help you to develop your plan for responding to identified risks.


Risk Management or Conflict Sensitivity: Which One Should I Be Doing?
The short answer is: both! Risk management and conflict sensitivity often work together, and some frameworks might combine the two. For example, the UNDP Risk Management framework noted above includes conflict sensitivity as one core principle. Conflict sensitivity is needed for effective risk management because doing harm, while usually unintended, can amplify risks to the organization, the program, or staff members themselves.
CDA has developed a set of questions that can help you integrate Do No Harm into your risk analysis and risk mitigation planning.
What do P/CVE risks look like?
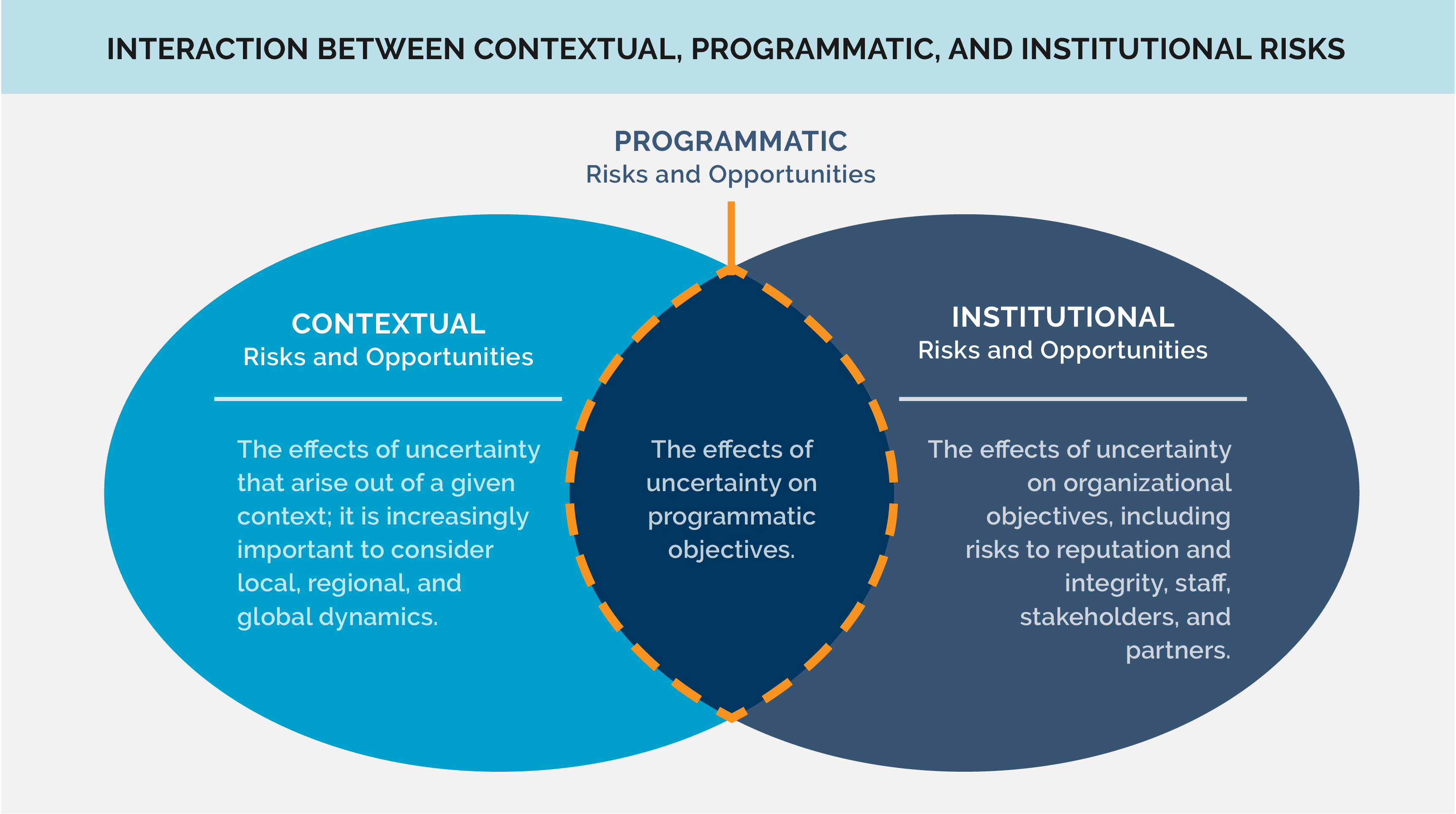
Risks will differ for each project based on the context and the organization implementing the project. Organizations can identify categories and/or types of risk that guide its risk management process. The UNDP Risk Management Framework identifies three categories of risks and opportunities - contextual, institutional, and programmatic.
The European Commission identified the following risk categories or types: Financial, Operational, Security, Legal, Political, Reputational, and Administrative.
This illustrative list reflects risks that other P/CVE projects or implementers have identified. The list is not comprehensive, but it can help your organization consider the categories and types of risks that could be relevant for your project.